After the not so well-received Vista operating system, the software giant Microsoft released Windows 7, which is, according to many, the best Windows operating system to date. It is fast, robust, user-friendly, and functional, and most users have responded to it extremely well, but while some are still contemplating whether to take the leap and purchase, install, and use Windows 7 on their personal computers, the company is already actively developing its successor, unofficially named Windows 8. Windows 8 has been the talk of the town for quite a few years, with leaked screenshots and Milestones appearing here and there, and it has been surrounded by many rumors and speculations. On June 1st Microsoft has finally spoken up and revealed some of its features and the concept behind it.
The Darwinian Evolution of Graphic Design – Infographic
The evolution of graphic design is a very is very interesting. It is hard to believe the way we do things now that thousands of years ago “graphic designers” were chipping pictographs into cave walls. While some designers would probably be much better at that than they are with Photoshop it is really fun to look back and also think about what is in store for the future of graphic design. Without further delay, here is The Darwinian Evolution of Graphic Design.
Network Attached Storage – What is it and who needs it?
As your business grows, so will the need for better and more efficient data storage and this is where a network attached storage can come in handy. The network attached storage devices are nothing more than a specialized device, which stores data and files, makes the data available to all other computer in the network, offers data protection, and enables you to assign different access permissions as well. On the outside, most of these devices look just like a normal PC or server, but unlike regular computers, most do not have keyboards, monitors, or mice attached to them. Typically, they also run a strip-down operating system, which allows them to do what they have been designed for efficiently, but not to be used as a fully functional server of computer.
14 Ways to Destroy Designers Block
Are you running low on creative ideas? Having a designer’s block? You are not alone and even the most talented and inspiring designers, authors, and artists are constantly looking for new sources of inspiration, and we have come up with a number of suggestions that you could find interesting and useful.
Hot Trends in Web Development
What makes the work of the web developer challenging and exciting at the same time are the ever-changing trends! With the exponentially increasing popularity of the mobile Internet surfing and the very strong user base of the social media sites, the latest design and development trends seem to be heading towards functional, less busy, and with larger logos and image backgrounds web sites, which incorporate the latest Web development technologies as well
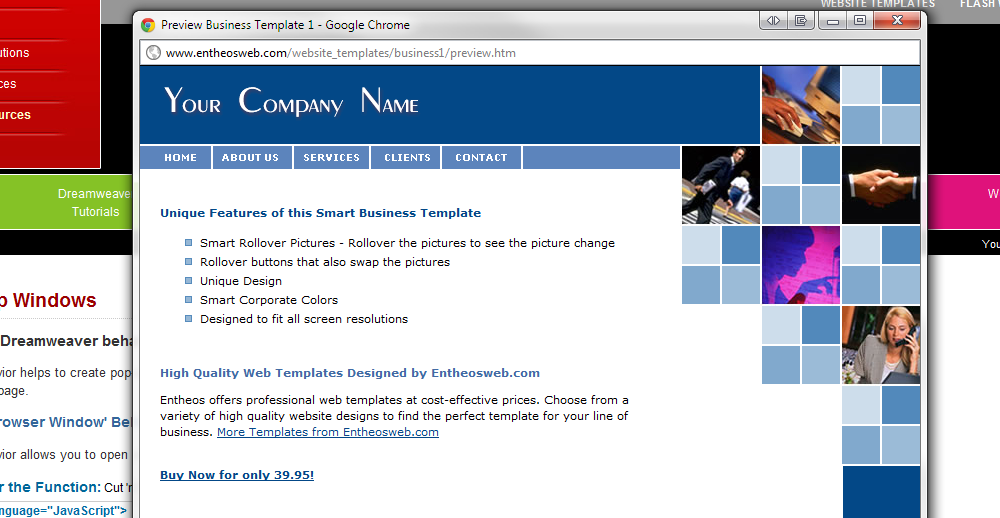
10 Web Design Mistakes to Avoid
Regardless if you are just starting out as a web designer or you have more than a few hundred designs under your belt, you could […]
Big Changes in Store for WordPress 3.2 – Check Them Out Here
Even though WordPress 3.1 was released only in February, WordPress 3.2 Beta 1is already available for download and it comes with a number of new features. The most notable of them are the new admin layout, the Full screen editor, which facilitates destruction free writing, the new Twenty Eleven theme, new PHP and MySQL requirements, the enhanced admin bar, and the faster loading speed. What else has changed in WordPress 3.2 and are these changes going to make the most popular Content Management System even better?
Summer is Approaching, Time to Find an Internship or Job
It’s that time of year again. Temperature on the rise, pants getting pleasingly shorter, free time increasing, money situation low. Well “Snoop Doggy Dogg”, it’s time you got yourself a “jobby job”. It’s not the best of times out there, especially for youngins on the come up. Unemployment for teens and young folk, students, is something like three times the national rate. Which is hovering in the crapper as is, something like 8-9%. Options are few and there are a lot of people out there aiming to take the jobs that you would normally be able to get during the summer to help pay for your long break from reality. Hopefully I can drop some knowledge on you with a few tips on how you might be able to land a summer job or internship to get you through til the shroud of school blankets you from the real world that us folks get to deal with all year full time.
Awesome Twitter Facts & Stats [Infographic]
There is no doubt about people love social networking. What do you think people would have said 30 years ago if you told them millions of people would enthusiastically communicate 140 characters at a time? They would probably tell you that you’re crazy and tell you to scram. Perhaps they would be correct, but you have to admin, Twitter and other social networks sure are entertaining.
How to Rip a CD Like a Pro – Part 7
Here we are, the 7th and final part of the ‘How to Rip a CD Like a Pro’ series. It has been a long road but I think it is a road that is well worth traveling. You can now rip your CDs and enjoy a great sounding file. So lets finish up the rest of the ripping guide and the settings for MP3 rips. I’ll stop talking and we’ll get this over with!
How to Rip a CD Like a Pro – Part 6
Holy crap, this CD ripping guide is going on forever! It seems like a while ago I started this guide and were getting to the actual ripping part! We’ve gone over setting everything up in the settings to rip your disk to FLAC files and form this point we’re going to let you know how to save those settings to a profile and the starting steps in ripping the files. So let’s get to it!
Ready to Launch? Things to Check Before Launching Your Site
You just finished what is, in your opinion, the most beautifully designed site you have ever worked on. Not only are you finished but you are ahead of schedule by a week, might as well launch the site and let the kudos from the customers pour in. As you expected you get a phone call minutes after the site goes live from your client and you answer it with joyous confidence…then the yelling begins. How can this be? The site design is awesome in every aspect, but apparently one. You forgot to update the alt tags from your filler, alt=”clients naked wife”, to what it should actually be. If only you had taken that extra week and poured over the site with a fine tooth comb this would not have been an issue. Here is a list of things to check and help you avoid this scenario.
RFID – Revolutionary Tech or Pure Evil?
RFID stands for radio-frequency identification and is the technology, which much similar to the barcode technology allows information to be exchanged between labels and readers. However, unlike the barcodes, this technology uses radio waves, which bring in a number of advantages and even though the barcodes have seen their fair share of evolvement and the latest symbologies offer much better reliability, readability, and can store more data, they have been around for more than forty years, and RFID is their most likely replacement.
The Wonderful World of Search – Top 10 Countries and What They Search For [Infographic]
It is interesting to see that the top searches by country vary just as much as the countries that make up the Top 10 countries on the internet. They do have one thing in common, there is at least one social network in each of the top 5 searches. I have to say though, one thing that always stumps me is why people search for sites like Facebook and Google instead of just going there directly. It is a mystery that will most likely never be solved.
Become a Google Master with these 20 Awesome Search Tips and Tricks
Google arguably has the most advanced technology and algorithm in all of website systems to date. But Google isn’t just a search engine for it doesn’t just find websites, people or products for you. With these 25 amazing Google search tip and tricks, Google can help you find almost anything.