Instagram advertising is a powerful and versatile tool for driving traffic, generating leads, and converting followers into customers. With over a billion monthly active users, […]
Mac vs PC – What to do after you have made the switch
So you have made that move, switched from a Windows machine to a new Mac. Maybe not you, but I did make that switch, and so far I have loved it. Loved it so much from an operating system and hardware standpoint I will not be going back. Making that switch though, you look for your familiar applications, what you use on a daily basis. Anymore a lot of items are universal, they make a version for Windows and a version for your Mac. There are a few out there still though that you need to find something similar. Some of them you may end up liking more. We’ll go over a few of those apps that are different, and a few similar or the same. But I will share that switch experience with you all and give you some direction on where to point your browser.
14 Tips to Speed up Your Personal Computer
1. Main Reasons for a Slow PC Several reasons exist for the slowing down of personal computers, which are not related to a malware attack […]
The Ol’ Switcharoo – PC User Switches to Mac
Having expendable income is a rarity in my life, so rare that it never happens. Having expendable income, a coupon for 20% off all laptops at Amazon.com, and the need to upgrade my four year old laptop is a sign from Odin, Zeus, or maybe Cthulhu that it is time to buy. In my search for what laptop I would like to own I narrowed it down to a mega gaming rig and a Macbook Pro. I have been an avid PC gamer for many years but as I have aged and since abandoning MMORPGs the need for a gaming rig has decreased a lot. I have been a fanboy of my iPhone and an envious iPad wanter for some time but to take the plunge into buying a true Apple computer. That is a big choice. I haven not used a Mac since high school. They were pretty freaking terrible back then too. Jumping from Windows 7 to OSX Snow Leopard, how hard would that be
Popular Design Blogs by Twitter Followers and Facebook Fans – Revisited [Infographic]
Ten months ago we published an infographic on the most popular web design blogs and their followings on both Twitter and Facebook. We decided to update that graphic and see where those same blogs stand today. As you an see the fans and followers have increased a good bit in the last ten months. Check it out!
CPU Faceoff – 32-bit versus 64-bit Technology
Processors have come a long way since the days of the 8088 and single core processor. In today’s world we now need to make a decision when installing Windows and other various operating systems. That question is: Should I install the 32-bt version or 64-bit version? Here is an explanation of the 64-bit processor which should help you decide.
Gaining and Understanding of Computer Forensics
Computer forensics is a very popular career choice, but what exactly is it? It is more than the stuff you see on CSI, and most likely not as glamorous.
How to protect your children online
Most children and adolescents use computers on a daily basis to do their homework, search for information, play computer games, socialize with friends, watch videos, and engage in various other activities. However, surfing the Internet comes with a number of dangers and it is their parents’ responsibility to protect their children from these dangers and teach them how to stay safe online. Quite often, this is easier said than done since many parents are not computer savvy and know far less about the cyber world than their kids. What are some of the steps that you need to take in order to make sure that your children are protected from harm when surfing the Internet?
History of Apple, Inc. – The Most Valuable Company In The World – Infographic
It was recently announced that Apple, Inc. is the most valuable publicly traded company in the world. I wonder what people say twenty years ago if you told them that this would happen, most likely they would have laughed in your face. Regardless, Apple is definitely doing something right. In honor of their great achievement here is our infographic, The History of Apple, Inc.
How Web Designers Can Effectively Communicate With Their Clients
Working from home brings numerous advantages and if you are freelancing web designer, you can decide which projects to take and work from the comfort of your own home. However, many independent web designers and developers do not realize the importance of communication successfully with their clients. Web design and development is business like any other and prompt and efficient communication is just as important as great designing and developing skills. Here are a few tips, which could help you keep that two-way communication channel open and your customers happy.
Need a New Camera? Check Out Our Digital Camera Buyers Guide
Digital cameras are amongst the most sought after gadgets. Right now, there are hundreds of digital camera manufacturers, offering thousands of models and with the vast array of digital cameras, it is often difficult for the consumer to pick the best model that he or she can afford. Most of us need cameras, which are easy to use, take excellent quality photos, shoot decent movies, and are small enough to fit in a shirt pocket. Of course, there are photographers, who take shooting pictures far more seriously and are after high-end models that offer better performance and have more features than the average point-and-shoot camera. Before buying a digital camera, you need to determine your own needs and decide if you are going to use the camera only on your next vacation, if you are more likely to take indoor pictures, or if you need a top of the range camera, which you can use with different lenses to take pictures in different shooting conditions. Once you have decided on the camera type, your budget, and your own needs, it is time to take a closer look at the different models’ specifications and pick the right one.
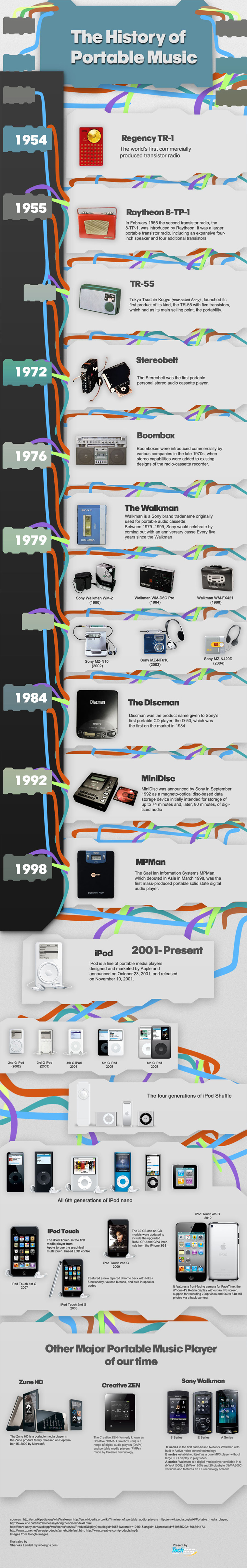
The Evolution of Portable Music – Infographic
I am old enough I remember when the Sony Walkman was the must have gadget. We have come a long way with portable music, just look at what we are using today as opposed to just 15 or 20 years ago. It makes me wonder, how did we survive without or iPhones and other gadgets of convenience?
Stunning Optic Fiber Light Rays Tutorial
Let’s play around a bit by creating a stunning optic fiber inspired light rays background (or pattern, texture, or brush, whichever way you think of it). Just a bit of Photoshop know-how and you’ll be able to do this tutorial in a matter of minutes.
Go Local – How Web Designers Can Find Local Business
Even though many people frown upon cold calling, it is still an effective way to get business, as long as it is executed properly. Do not call indiscriminately, but rather limit the number of local businesses that you are trying to contact, learn a few details about their operation, pick up the phone, and explain how you can help them grow and profit from your services.
Battle of the Social Networks: Google+ vs Facebook
After Google Buzz and Wave, which never really took off, Google is launching its most powerful social networking project to date, Google+. At the time of this writing, you can join Google+ by invite only, but the interest is so great that many believe that Google finally got it right and Facebook has its first real rival. While the features, which Google+ offers are nothing revolutionary, the project seems to have taken the best from the other social networking sites, making it extremely easy for people to stay in touch with friends and family. It is still very early to judge if Google+ will make a dent in the Facebook’s business and take away some of their 700-million strong user base, but it is clear that the two social networks have quite a few features in common, but also differ in many aspects.